SANS Penetration Testing | SANS Poster: Building a Better Pen Tester - PDF Download | SANS Institute
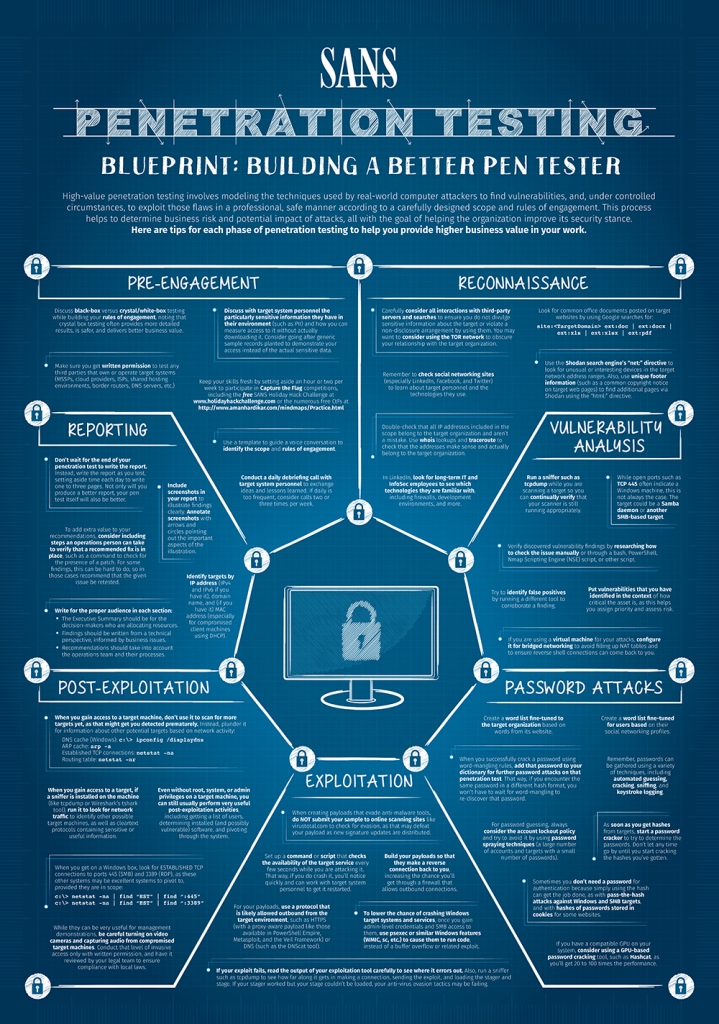
SANS Penetration Testing | SANS Poster: Building a Better Pen Tester - PDF Download | SANS Institute

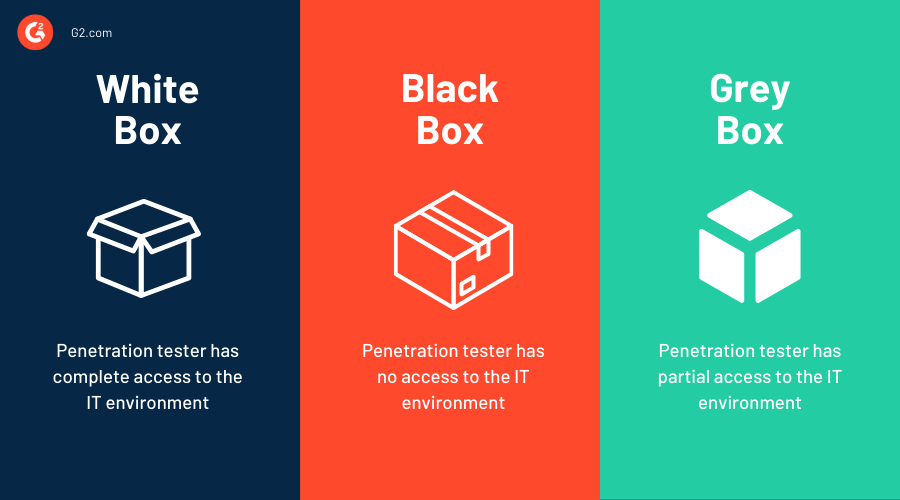
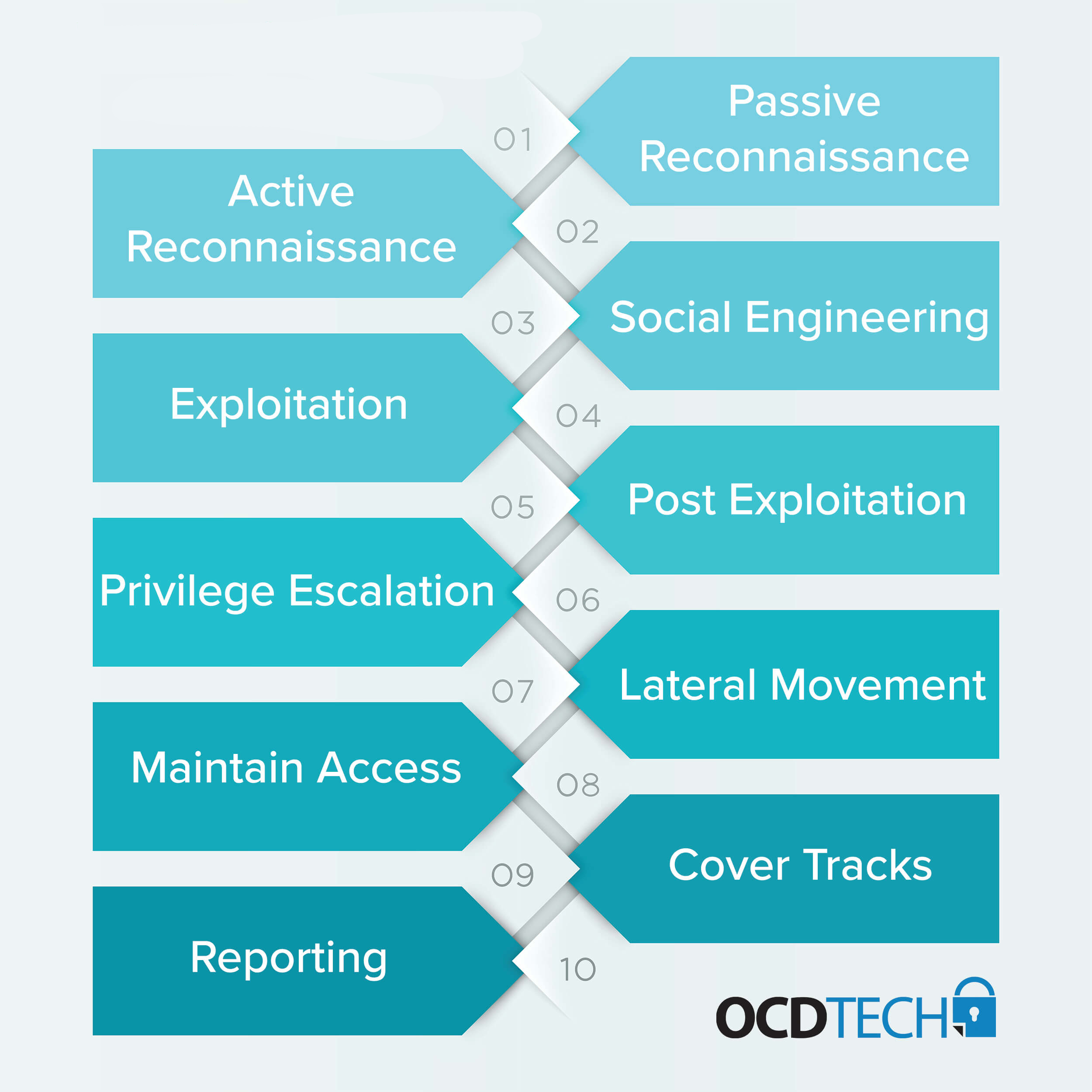
The simulated security assessment ecosystem: Does penetration testing need standardisation? - ScienceDirect
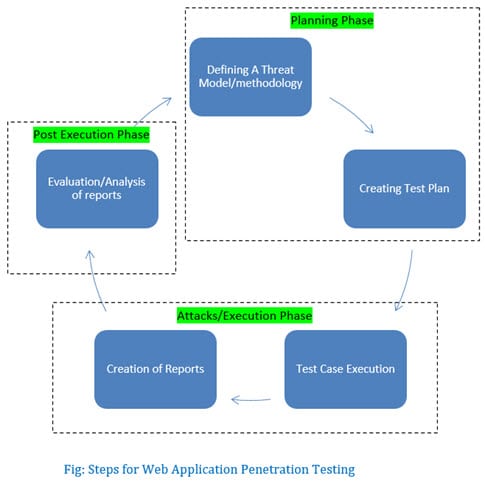
![PDF] Port and Vulnerability Scanning, Packet Sniffing, Intrusion Detection, and Penetration Testing free tutorial for Advanced PDF] Port and Vulnerability Scanning, Packet Sniffing, Intrusion Detection, and Penetration Testing free tutorial for Advanced](https://www.computer-pdf.com/documents/covers/0729-port-and-vulnerability-scanning-packet-sniffing-intrusion-detection-and-penetration-testing.pdf.png)




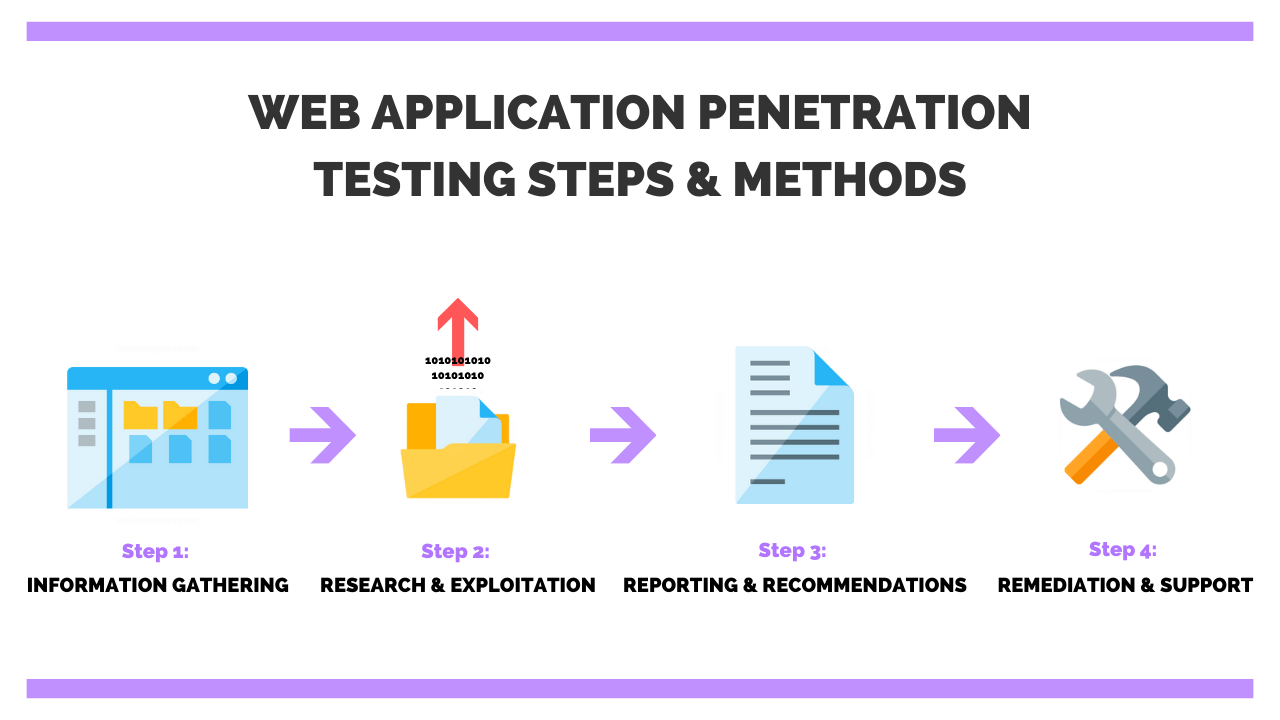

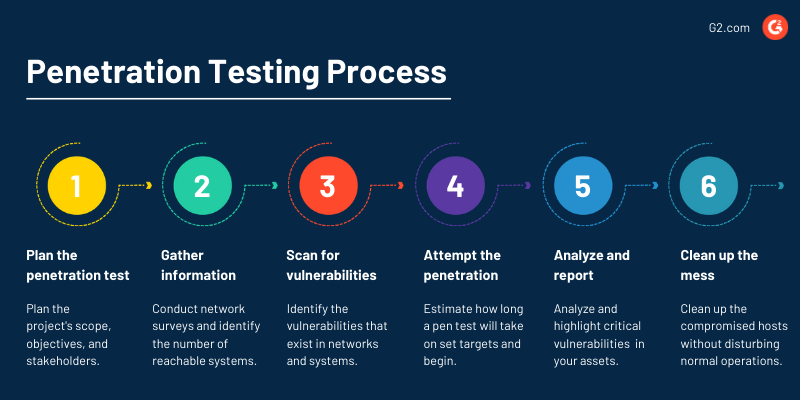
![PDF] An Overview of Penetration Testing | Semantic Scholar PDF] An Overview of Penetration Testing | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/47ab031ed57e76b539cae466f376d745ccc18e28/4-Figure1-1.png)